
 | MAPSANDS™ is an autonomous, intelligent, fully integrated wide area perimeter security and access denial system. MAPSANDS™ was specifically developed for large wide area perimeter applications such as international and sovereign borders, oil & gas infrastructure and other high value critical asset installations. MAPSANDS™, unlike traditional perimeter security solutions, is a fully programmable, integrated autonomous system that can monitor, detect, track, target, warn, establish intent, deter, and if necessary deliver a non-lethal response to the would be aggressors, subject to compliance with applicable laws, regulations and treaties. |

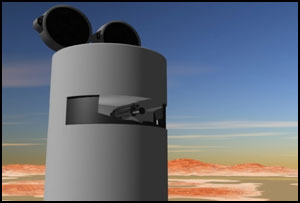
MAPSANDS™ system architecture was designed to secure areas from less than one mile to several hundred continuous miles through the integration of a series of sensors and transducers that collect and share data, analyze it and deliver a programmed response based on predetermined rules of engagement. MAPSANDS™ relies on directional non-lethal high frequency focused acoustical transducer arrays to project verbal warnings and aversive warning tones to intruders. These devices are designed to be effective at ranges in excess of 1000 meters and support determining an approaching individual(s) intent. Additionally an advanced programmable airburst munitions delivery system, from Vision Technologies System (VTS) has also been integrated into MAPSANDS™ and is capable of accurately targeting and dispersing other non-lethal deterrents, such as tear gas, malodorants or pepper spray at ranges in excess of 1500 meters. |   |
 |
MAPSANDS™ uses a network of real time position sensors to provide detection, tracking and targeting coordinates. These coordinates are continuously feed to the transducer arrays and the airburst munitions system in order to insure accurate targeting once the system has been engaged by an aggressor(s). |
MAPSANDS™ rules of engagement are programmable however typically rely on:
1.) THREAT DETERMINATION: In this case targets are identified when movement is detected within the position sensors scan range. Target threats are quantified by the target distance from the designated border/perimeter. The closer the target the higher the threat and subsequently the level of response. The system remains configurable for number of threat levels as well as their distance from the designated border/perimeter. 2.) THREAT PRIORITIZATION: In the case of multiple targets prioritization response is based on projected time to reach the designated border/perimeter. This determination is computed using the target's perpendicular approach speed. This applies to targets on the same threat level. Once a target has crossed into a higher threat/response zone, it will be designated the highest priority, the remaining targets shall be prioritized based on their approach speed, but at lower levels than the closest target. Prioritization determines the response resource allocation. Targets are allocated resources - for example acoustical array warning tones or airburst munitions delivery - based on their threat priority. Resource allocation cycles through the targets in their prioritized order until the targets retreat, become neutralized or all resources have been exhausted. |  |
3.) BASIC RULES: Overall, the rules are applied to threat targets to determine the response, and then to execute the response. The rules are configurable on a per-cell basis.
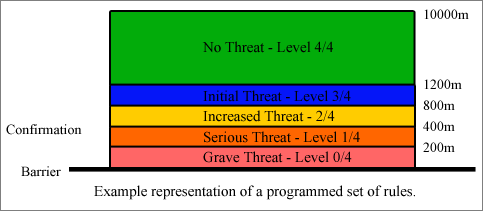
In the above figure, the layered threat thresholds are highlighted in different colors. The barrier line represents the object being protected. The number of threat thresholds - in this case five - shall be configurable. The distances - in this case represented on the right side of the layers - shall be configurable. The responses for each level shall be configurable, as is the manual confirmation requirement.
The following responses shall be available for assignment to a level. For illustration purposes, their possible assignments to the above example are provided.
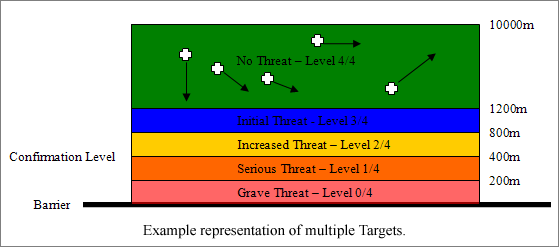
In the above Multiple-Target representation, multiple targets are identified but are all within the Level 4 Zone. The arrow represents the direction of movement of each target. In this case, the system prioritizes the targets by their predicted arrival at the barrier, based on their speed and heading. Until a target crosses the threshold into the next level of protection, these targets are tracked and logged, and assigned the appropriate response for the level.
As soon as a target crosses into the next protection level zone, it is assigned the highest priority, and receives the appropriate response.
The system can be programmed to concentrate only on the most serious threat (the target closest to the barrier) or to cycle through the targets issuing the appropriate responses, but assigning the resources to the most serious threat more often.

Resource allocation interleaving in the case of multiple Targets at different levels
MOBILE MAPSANDS™: Although the initial focus of MAPSANDS™ has been to provide autonomous perimeter security for fixed installations, borders, and other critical infrastructure, on Nov 11, 2005 MAPSANDS™ was successfully demonstrated by US Global Nanospace as a rapidly deployable mobile system applicable for commercial, civil, national and international disaster, security and defense related applications.

